Cybersecurity Monthly Report (March 2024)
Ex ante coordinative defense and monitoring
A total of 53,440 pieces of government agency cybersecurity coordinative defense intelligence were collected this month (an increase of 5,528 from the previous month). Analyzing the types of identifiable threats, the top identifiable threat was information collection (40%), i.e., mainly obtaining information through attacks such as scanning, detection, and social engineering. This was followed by hacking attempts (20%), which were mainly attempts to hack unauthorized hosts; and intrusion attacks (12%), most of them involving unauthorized access to systems or acquisition of system/user privileges. The distribution of intelligence volume in the past year is as shown in Figure 1.
Upon further analysis of coordinative defense intelligence, it was found that hackers took advantage of the recent data leak news and send social engineering e-mails to government agency personnel. The subject line of the e-mails stated that conclusive evidence was found that the government of a certain country hired hackers to attack a neighboring country. The relevant information has been provided to agencies with recommendations for coordinative defense, monitoring, and protection.
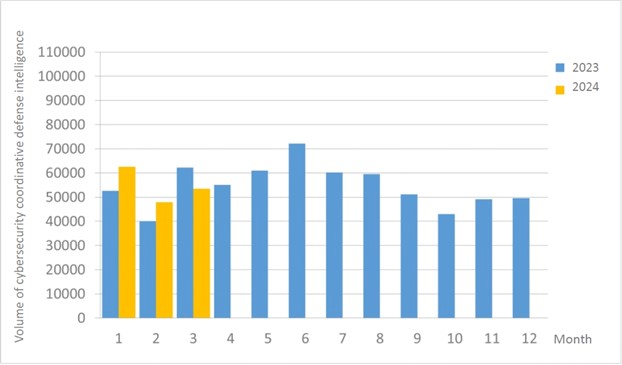
Figure 1 Statistics of cybersecurity monitoring intelligence in coordinative defense
In-process reporting and responding
The number of cybersecurity incident reports totaled 83 this month (an increase of 10 from the previous month), a 13.7% increase from the previous month. Certain agencies were hacked and attacked with malware. This occurred because the agencies were using a shared administrative system with security vulnerabilities provided by another agency that did not restrict access to the Internet. This incident accounts for 13.2% of “illegal intrusions.” The statistics of cybersecurity incident reports in the past year are as shown in Figure 2.
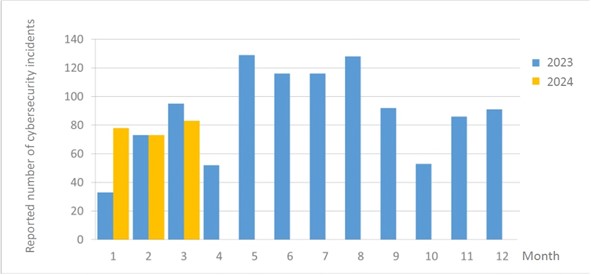
Figure 2 Number of reported cybersecurity incidents
Post information sharing
The National Institute of Cyber Security found that certain government agency repeatedly connected to a relay station. The incident was caused by malware in the form of a fake LINE instant messaging application. During the investigation, it was found that the agency had been repeatedly connecting to the same relay station since January of this year. The agency was contacted, which it stated that it had reset the hacked host, reviewed and updated its systems, advised users to download the correct version of the application from the official website, and asked the provider to help set up a firewall to block the relay station. However, it was later found that the agency only made verbal announcements without verifying users' behavior and implementation by the provider. This led to repeated connections to the same relay station.
Additional Reference:
When a cybersecurity incident occurs, the root cause of the incident should be analyzed. Based on the analysis, effective operational enhancements and improvement measures should be proposed and implemented. However, some agencies may have limited manpower and resources and therefore handle cybersecurity incidents only by restoring their information environment. Such agencies fail to identify the root cause of the incident, take effective control and management measures, or implement improvement measures. This results in the recurrence of cybersecurity incidents. To reduce the risk of cybersecurity incidents, downloading or installation of software by users should be restricted or regulated. In addition, consideration should be given to implementing improved procedures (this includes reviewing steps taken by contracted suppliers). If cybersecurity incidents continue to occur, the root causes and responses should be carefully investigated to ensure that the risk is managed.