Cybersecurity Monthly Report (April 2024)
Ex ante joint defense and monitoring
A total of 51,512 pieces of government agency cybersecurity joint defense intelligence were collected this month (a decrease of 1,928 from the previous month). Analyzing the types of identifiable threats, the top identifiable threat was information collection (56%), i.e., mainly obtaining information through attacks such as scanning, detection, and social engineering. This was followed by hacking attempts (15%), which were mainly attempts to hack unauthorized hosts; and intrusion attacks (12%), most of them involving unauthorized access to systems or acquisition of system/user privileges. The distribution of intelligence volume in the past year is as shown in Figure 1.
After further compilation and analysis of joint defense intelligence, it was discovered that hackers have recently impersonated a state-owned enterprise and used subjects related to the enterprise’s business to send social engineering e-mails to attack devices of government agencies and the general public. Analysis shows that hackers stole the contents of e-mails that people had exchanged with the company in the past, using them as baits to include malicious attachments. The large scale spreading of malicious spam e-mails was used to carry out social engineering attacks.
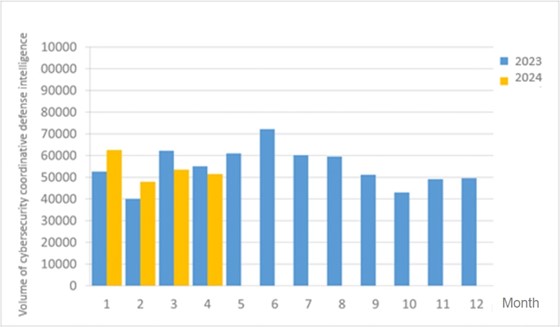
Figure 1 Statistics of cybersecurity monitoring intelligence in joint defense
In-process reporting and responding
The number of cybersecurity incident reports totaled 127 this month (an increase of 44 from the previous month), which is 2.44 times the number of reports in the same period last year. In addition to the impact of the April 3 earthquake on service availability, the National Institute of Cyber Security found that information devices from multiple agencies exhibited malware characteristics or other suspicious connection behavior, accounting for 44.09% of the total number of reports. The statistics of cybersecurity incident reports in the past year are as shown in Figure 2.
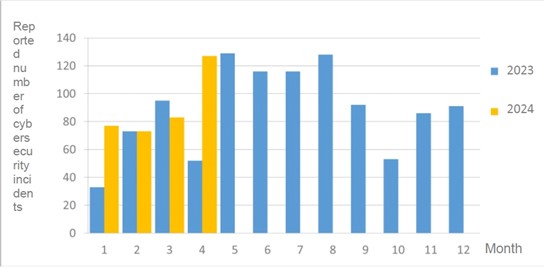
Figure 2 Number of reported cybersecurity incidents
Post information sharing
This month, hackers used the File Transfer Protocol (FTP) service to upload mining programs to the printers and security cameras of certain government agencies. After an investigation by the agency, it was found that the FTP service of the hacked devices was publicly accessible and used weak or default passwords. It was concluded that the hackers decrypted the passwords and uploaded the mining programs after logging in. The agency concluded that the devices did not require public access and disconnected them from the network or restricted them to internal IP access to mitigate similar cybersecurity risks.
Office devices such as printers or security cameras are primarily intended for the internal processes of an organization. Exposing such devices to external Internet access increases the security risk of unauthorized access or attacks. In addition, some devices support the FTP service for transferring files for printing or storing data. However, this service can be misused to implant malicious programs. When setting up such devices, agencies should consider the need for external access and ensure that all default passwords have been replaced with strong passwords. If the devices need to be publicly accessible, agencies should ensure that only essential services are accessible and that the firmware of the devices is regularly updated to minimize the risk of intrusion.