Cybersecurity Monthly Report(August 2024)
Ex ante joint defense and monitoring
A total of 90,510 pieces of government agency cybersecurity joint defense intelligence were collected this month (an increase of 13,938 from the previous month). This is mainly due to the recent increase in malwares detected (an increase of more than 9,000 pieces). However, the current information security mechanism has been successful blocking most malicious behaviors. Analyzing the types of identifiable threats, the top identifiable threat was information collection (38%), i.e., mainly obtaining information through attacks such as scanning, detection, and social engineering.This was followed by intrusion attacks (23%), most of them involving unauthorized access to systems or acquisition of system/user privileges;and malwares (17%), which were mainly detected when the hosts appear to be connecting to or downloading malwares. The distribution of intelligence volume in the past year is as shown in Figure 1.
After further compilation and analysis of joint defense information, it was discovered that hackers had recently sent social engineering e-mails in order to attack government agencies. These e-mails contained fake content informing Outlook service updates and phishing links, requesting the recipients to click on the link in the e-mail to log in and complete the service updates. Hackers deceive recipients through the subject and content of e-mails, attempting to trick recipients into providing sensitive information after clicking on the phishing links. Relevant intelligence has provided government agencies with recommendations on joint defense and monitoring.
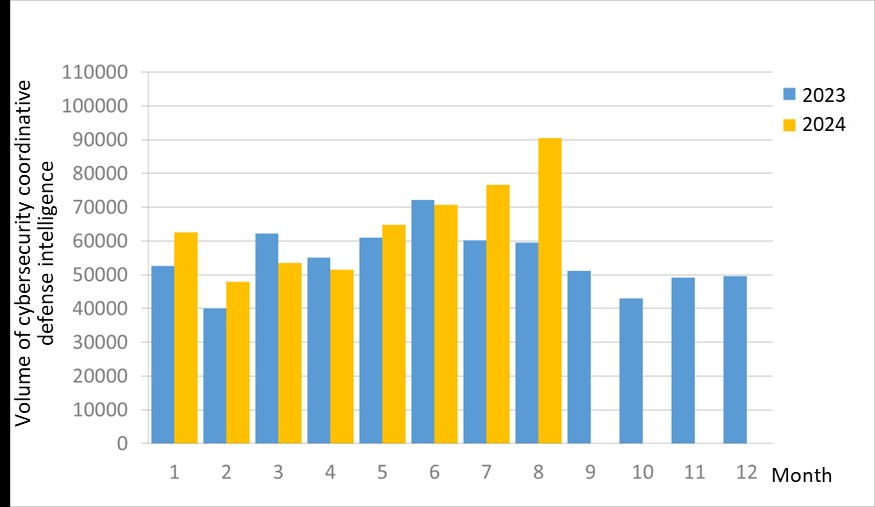
Figure 1 Statistics of cybersecurity monitoring intelligence in joint defense
In-process reporting and responding
The number of cybersecurity incident reports totaled 175 this month (a decrease of 101 from the previous month), a 0.36-fold increase compared to the same period last year. This is mainly due to the relatively high number of successful attacks related to military exercises. The statistics of cybersecurity incident reports in the past year are as shown in Figure 2.
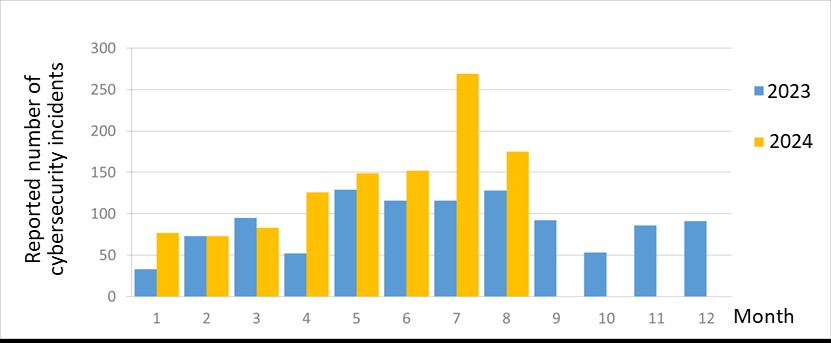
Figure 2 Number of reported cybersecurity incidents
Post information sharing
Recently, vulnerability checks on government agency websites are carried out adopting Google search operators. Multiple government agency websites were found redirected to gambling websites, the agencies were thereby determined to be subjected to “redirect hacking” that involves tampering the body and meta tags in HTML source code of the webpage, modifying the configuration settings in .htaccess files, and embedding multiple redirect HTML files. The aforementioned agencies, whose websites have been tampered with or have redirected files implanted, choose to rebuild the website environment and conduct vulnerability scanning to repair and strengthen the website security.
Additional Reference:
Redirect Hacking is a type of cyberattack where an attacker controls or hijacks a user's network traffic. The attacker usually takes advantage of website security vulnerabilities to modify website parameters or insert links, and thereby leads users browsing legitimate websites to other malicious websites. Agencies are recommended to establish information system management principles, such as conducting security testing before launching the system, reviewing the security of the service system through regular testing mechanisms such as vulnerability scanning and penetration testing, and tracking website changes with monitoring tools to immediately detect unusual changes.