Cybersecurity Monthly Report (December 2024)
< Recent Cyber Security Campaigns >
To help government agencies improve their cyber security protection, the Administration for Cyber Security selects agencies' external websites to conduct penetration test exercises every year. The top three types of vulnerability found in 2024 exercises and the suggestions for improvement are summarized as follows. All government agencies are requested to review and strengthen information security protection measures:
- Encryption Mechanism Failure: Some employees in government agencies only use the built-in masking function in PDF software to hide sensitive data, which is easy to be cracked. It is recommended to convert the masked data into an image format to ensure the masking effect.
- Injection attacks: The input function of some web services is still vulnerable to code injections by attackers, which can easily lead to hacking breaches, so it is important to thoroughly test and patch these issues, as well as filter common special characters such as “ ‘ < > * -- % $ ; etc.
- Invalid access control: The file download links of some websites can obtain non-public information by modifying the path, so we should set up data access control, strengthen the path verification, and implement the principle of least privilege.
< Overall Threat Trend >
Ex ante joint defense and monitoring
A total of 83,105 pieces of government cybersecurity joint defense intelligence were collected this month (a decrease of 13,070 from the previous month). Analyzing the types of identifiable threats, the top one was information collection (52%), i.e., mainly obtaining information through attacks such as scanning, detection, and social engineering; followed by intrusion attacks (21%), most involving unauthorized access to systems or acquisition of system/user privileges, and intrusion attempts (16%), most dominated by attempts to intrude into unauthorized hosts. The distribution of intelligence volume in the past year is as shown in Figure 1.
After further compilation and analysis of joint defense information, it was discovered that hackers, under the guise of presenting administrative suggestions to government agencies (such as petition cases), used third-party email service accounts to launch a spear-style social engineering email attack targeting specific agencies. The attack involved attaching a compressed file containing petition opinions, which tricked the recipient into opening a malicious file, allowing the hackers to implant a backdoor program and steal sensitive computer information. Relevant intelligence has provided government agencies with recommendations on joint defense and monitoring.
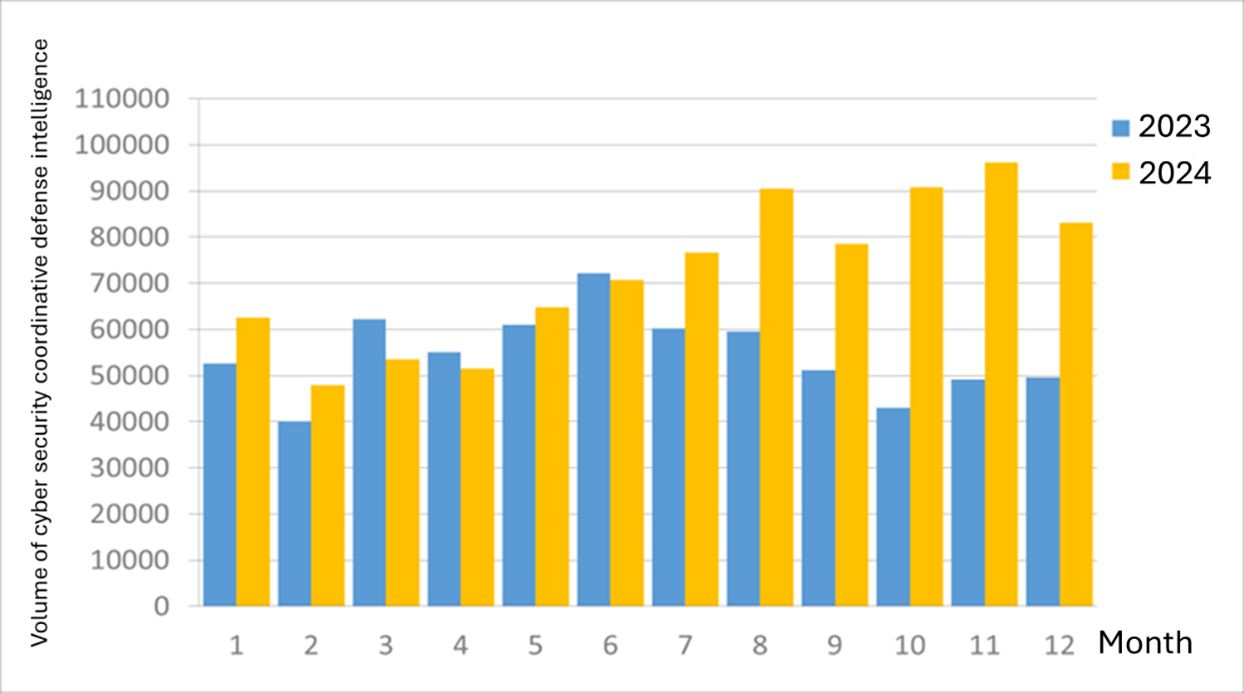
Figure 1 Statistics of cybersecurity monitoring intelligence in joint defense
In-process reporting and responding
The number of cybersecurity incident reports totaled 40 this month (a decrease of 13 from the previous month), a 0.44-fold decrease compared to the same period last year. This month, it was found that some government IT equipment connected to malicious relay stations, downloaded malicious programs, or generated connections with features of data-stealing software and other malicious programs, which accounted for 47.5% of the total number of reports. The statistics of cybersecurity incident reports in the past year are as shown in Figure 2.
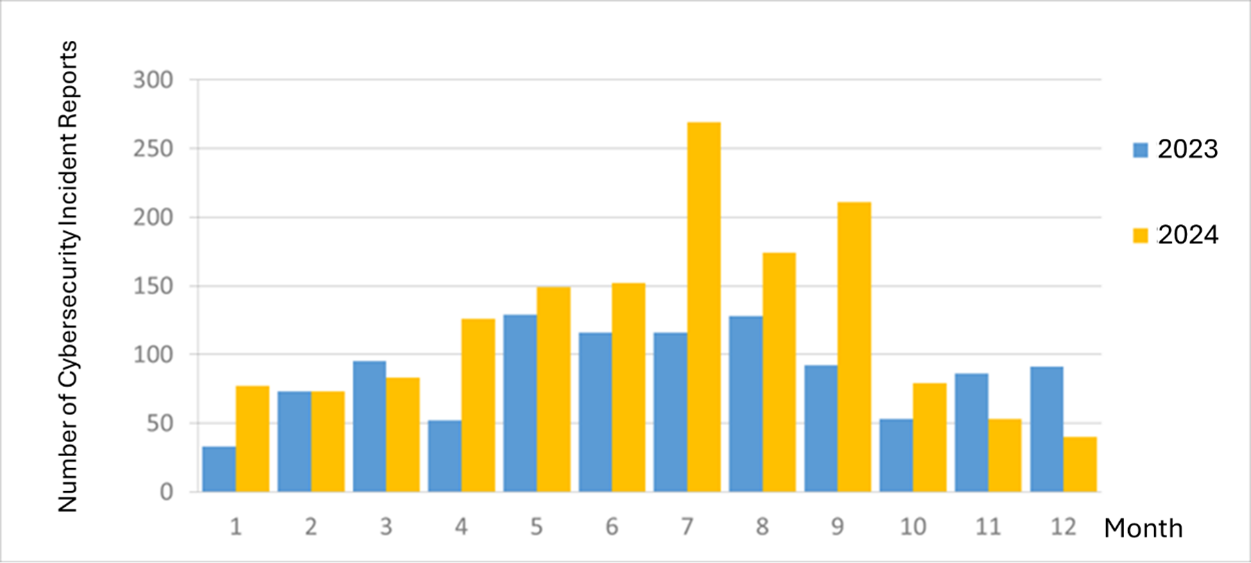
Figure 2 Number of cybersecurity incident reports
Post information sharing
This month, a certain agency discovered that an external IP successfully accessed the internal environment via VPN, then logged into the internal system and exported sensitive data. After investigation, it was found that the attacker used the VPN and internal system account name and password obtained from the previous security incident to successfully log into the internal system and steal data. As a result, the agency immediately disabled the relevant accounts and required all VPN accounts to be bound with mobile verification codes to strengthen the verification mechanism and reduce cybersecurity risks.
Additional Reference:
When the agency was conducting a cybersecurity incident recovery operation, in addition to fixing the problems found in the incident, the organization should conduct a comprehensive inventory of all possible leaked information and change the passwords or suspend the operation of the affected accounts to ensure that the leaked information will not become an entry point for subsequent attacks. Besides, VPN is an important channel for external connection to internal systems, and should be strictly controlled (prohibited in principle, allowed by exception, and limited to short-term opening). It is recommended that all VPN accounts be enabled with multi-factor authentication (e.g., mobile phone authentication code), regular review of usage records and abnormal behavior, and the establishment of a real-time alert mechanism to instantly detect and manage abnormal situations to reduce information security risks.