Cybersecurity Monthly Report (February 2025)
Cybersecurity Monthly Report (February 2025)
<Overall Threat Trend>
Ex ante joint defense and monitoring
A total of 64,531 pieces of government agency cybersecurity joint defense intelligence were collected this month (a decrease of 15,035 from the previous month). Analyzing the types of identifiable threats, the top one was information collection (39%), mainly obtaining information through attacks such as scanning, detection, and social engineering; followed by intrusion attacks (34%), most involving unauthorized access to systems or acquisition of system/user privileges; and intrusion attempts (14%), most dominated by attempts to intrude into unauthorized hosts. The distribution of intelligence volume in the past year is as shown in Figure 1.
After further compilation and analysis of joint defense information, it was discovered that hackers had recently been impersonating the Ministry of Finance and launching social engineering email attacks on government agencies and Taiwanese companies under the guise of a tax investigation. They have targeted financial personnel with access to sensitive information, inducing them to open and click on malicious links in attached files. Relevant intelligence has provided government agencies with recommendations on joint defense and monitoring.
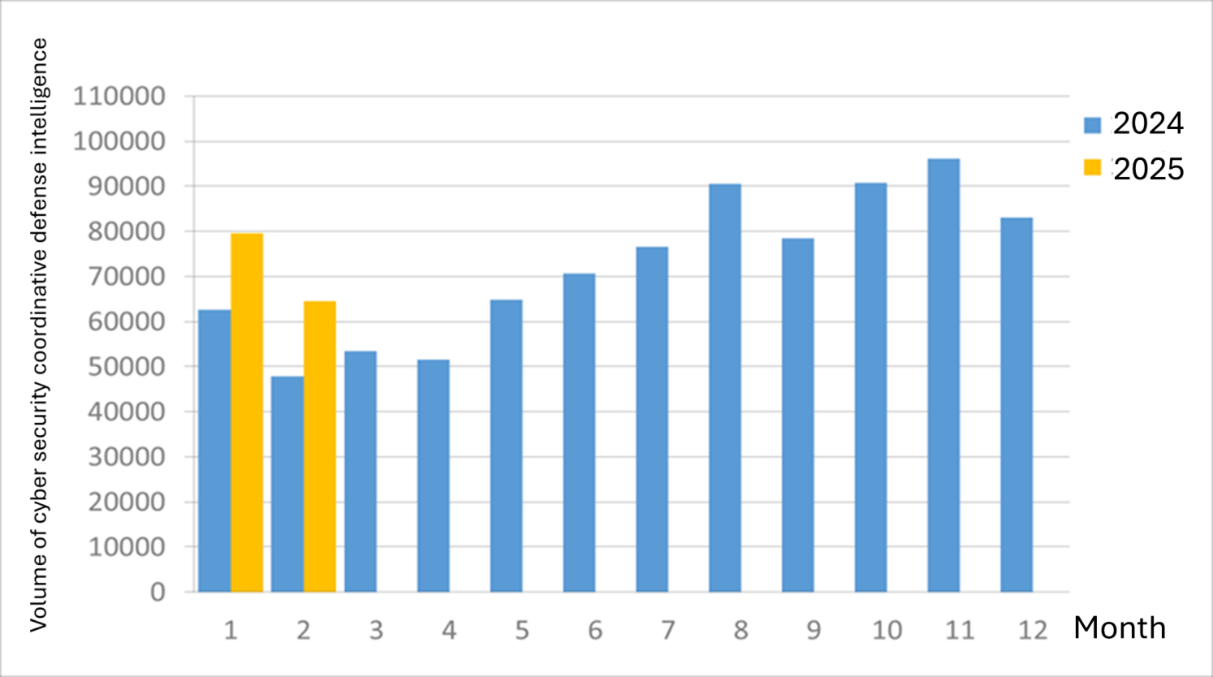
Figure 1 Statistics of cybersecurity monitoring intelligence in joint defense
In-process reporting and responding
The number of cybersecurity incident reports totaled 60 this month (an increase of 13 from the previous month), a 17.81% decrease compared to the same period last year. This month, the National Institute of Cyber Security discovered that multiple agencies may have installed counterfeit software, which generated connections with malware characteristics, accounting for 20% of the reported incidents this month. The statistics for cybersecurity incident reports over the past year are as shown in Figure 2.
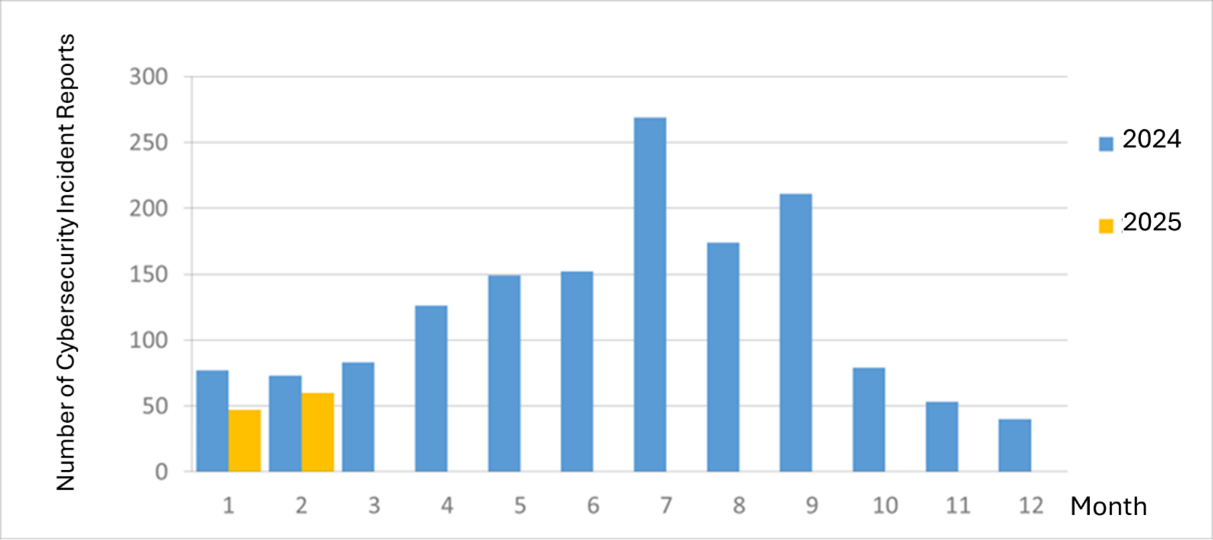
Figure 2 Number of cybersecurity incident reports
Post information sharing
This month, an agency found that an employee's computer was running an unknown program and generating abnormal external connections. After investigation, it was found that the attacker sent a resume with a malicious attachment through a job search website. The employee downloaded the attachment due to business needs and found a file suspected of being an Excel spreadsheet. However, the file was actually an Excel add-in (XLL) executable. Upon executing the file, the employee triggered the execution of the malware program, which led to the invasion of the computer and the abnormal external connection.
【Additional Reference】
Social engineering attacks are common hacker tactics. Recently, it has been found that hackers not only launch social engineering attacks through emails or the functions of an organization's website but also send malicious files or links through external websites used by the organization's businesses (e.g., job search websites, cloud file sharing services, and social media platforms, etc.). By taking advantage of the trustworthiness of such websites, they lure employees to download and execute malware programs, thereby infiltrating the internal network.
To reduce the risk of such attacks, it is recommended that organizations enhance employees' ability to recognize social engineering attacks. In particular, when using external websites, employees should carefully examine the attachments and links to avoid executing malicious programs due to misjudgment of file names, icons, or file formats. In addition, it is advised that organizations refer to the Government Configuration Baseline (GCB) settings and block Excel XLL add-ins from untrusted sources or, based on business needs, completely disable application add-ins to reduce the risk of information systems being loaded with malicious code via Office plug-ins.