Cybersecurity Monthly Report (March 2025)
Cybersecurity Monthly Report (March 2025)
< Overall Threat Trend>
Ex ante joint defense and monitoring
A total of 75,246 pieces of government agency cybersecurity joint defense intelligence were collected this month (an increase of 10,715 from the previous month). Analyzing the types of identifiable threats, the top one was intrusion attacks (37%), most involving unauthorized access to systems or acquisition of system/user privileges; followed by information collection (33%), mainly obtaining information through attacks such as scanning, detection, and social engineering; and intrusion attempts (14%), most dominated by attempts to intrude into unauthorized hosts. The distribution of intelligence volume in the past year is as shown in Figure 1.
After further compilation and analysis of joint defense information, it was discovered that hackers had recently been impersonating corporate legal departments and falsely claiming copyright infringement to trick email recipients into clicking phishing links in emails and filling out complaint forms, aiming to steal sensitive information. Relevant intelligence has provided government agencies with recommendations on joint defense and monitoring.
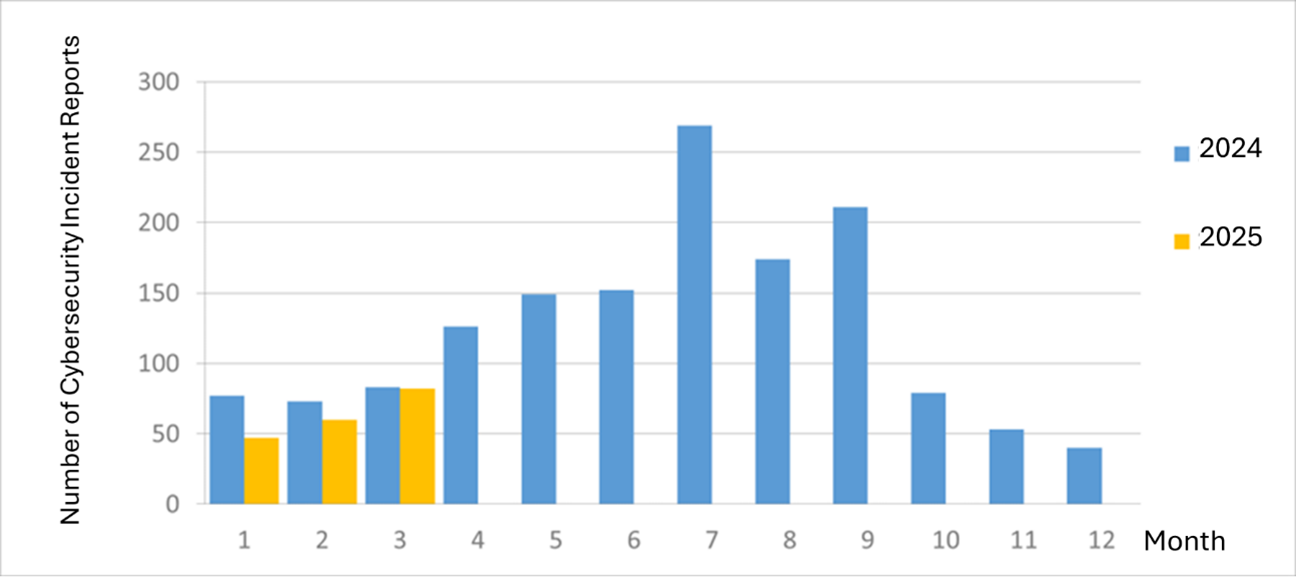
Figure 1 Statistics of cybersecurity monitoring intelligence in joint defense
In-process reporting and responding
The number of cybersecurity incident reports totaled 82 this month (an increase of 22 from the previous month), a 1.20% decrease compared to the same period last year. This month, some agencies were under the attack of blocking services, resulting in slowdown or interruption of website services, accounting for 30.49% of the reported incidents this month. The statistics for cybersecurity incident reports over the past year are as shown in Figure 2.

Figure 2 Number of cybersecurity incident reports
Post information sharing
This month, multiple agencies were found to have made outbound connections of malicious software characteristics. After investigation, it was found that users, while searching for the Line app through search engines, were misled by fake websites using '.com' domains with 'line' in the name. These deceptive sites appeared to be official download pages, leading users to unknowingly install Line installers bundled with backdoor malware. The affected agencies reinstalled the compromised computers and strengthened internal cyber security awareness to reduce related cyber security risks.
【Additional Reference】
Registering domain names that closely resemble well-known brands is a common tactic used in domain-based frauds. This includes using misspelled domain names, look-alike characters to create confusion, or fraudulent subdomains for fraud. These fake domains often use popular generic top-level domains (such as .com, .net, or .org) to appear more legitimate, aiming to steal personal data, financial information, or launch other forms of cyberattacks. Agencies are advised to not only strengthen endpoint protection, such as deploying Endpoint Detection and Response (EDR) solutions to identify abnormal behavior, but also to enhance cyber security awareness among users, reminding staff to download and install software only from official websites. In addition, depending on actual needs, agencies can also consider implementing application whitelisting to prohibit unauthorized software installations on government computers. Further, publishing and maintaining a list of approved software and official download links, as an institutional approach, can reduce user-related risks and improve overall cyber security protection.。