Cybersecurity Monthly Report (April 2025)
Cybersecurity Monthly Report (April, 2025)
< Overall Threat Trend>
Ex ante joint defense and monitoring
A total of 72,788 pieces of government agency cybersecurity joint defense intelligence were collected this month (a decrease of 2,458 from the previous month). Analyzing the types of identifiable threats, the top one was information collection (37%), mainly obtaining information through attacks such as scanning, detection, and social engineering, followed by intrusion attacks (33%), most involving unauthorized access to systems or acquisition of system/user privileges, and intrusion attempts (14%), most dominated by attempts to intrude into unauthorized hosts. The distribution of intelligence volume in the past year is as shown in Figure 1.
After further compilation and analysis of joint defense information, it was discovered that hackers have recently been distributing malicious spam emails containing Program Information Files (PIF). These emails exploit the ability of PIF files to conceal their file extensions, misleading recipients into thinking the attachments are normal documents. This tactic increases the likelihood of users opening the files and inadvertently connecting to malicious command-and-control servers. The relevant threat intelligence has been shared with all agencies, along with recommended measures for joint defense monitoring and protection.
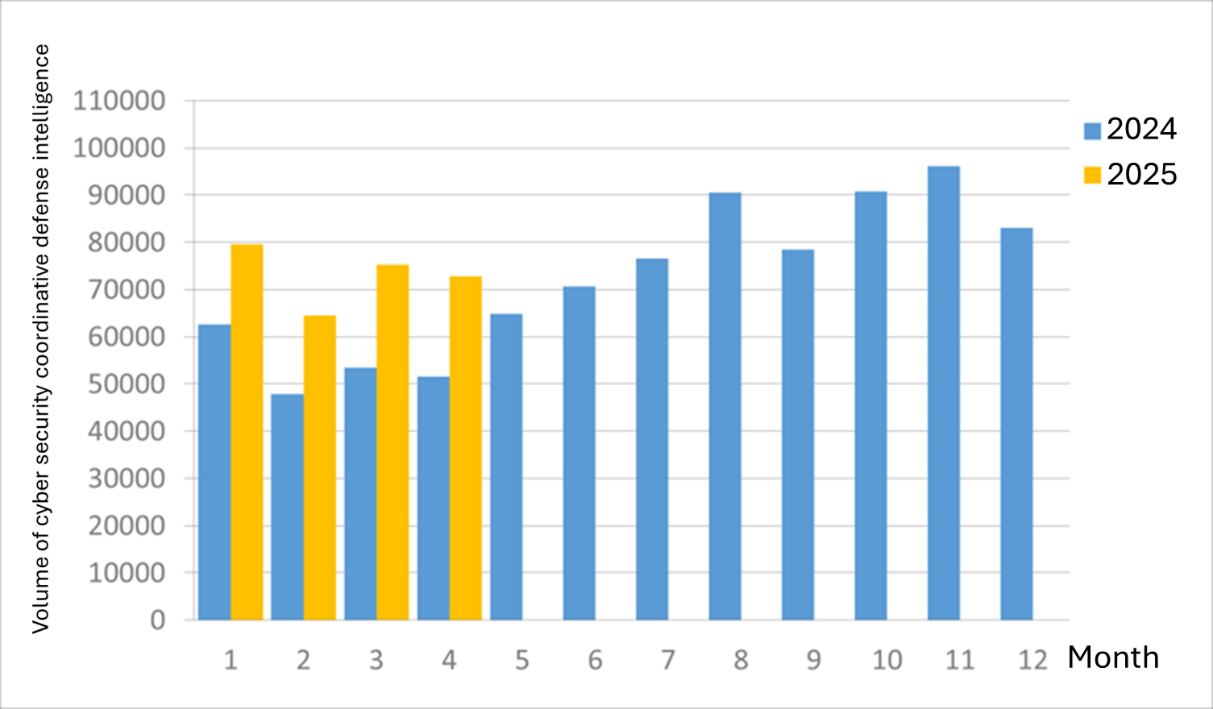
Figure 1 Statistics of cybersecurity monitoring intelligence in joint defense
In-process reporting and responding
The number of cybersecurity incident reports totaled 80 this month (a decrease of 2 from the previous month), a decrease of 36.51% compared to the same period last year. The majority of reported incidents this month were classified as unauthorized intrusions, accounting for 66.25% of all cases. Several agencies experienced abnormal connections with their information systems or showed signs of potential backdoor access being established. The statistics of cyber security incident reports in the past year are as shown in Figure 2.
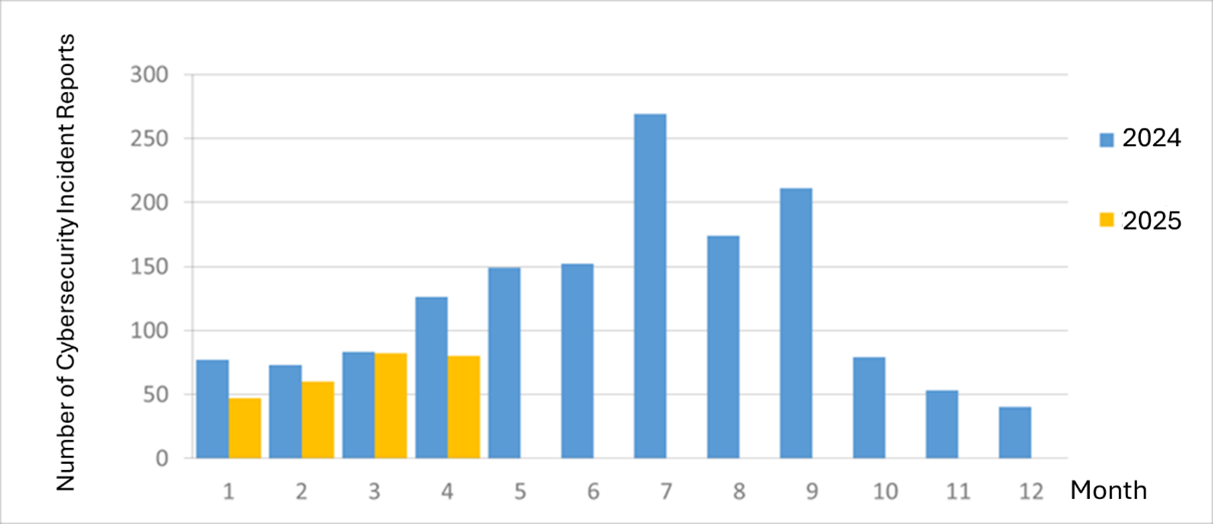
Figure 2 Number of cybersecurity incident reports
Post information sharing
During this month, the National Institute of Cyber Security identified that some agencies were using firewall devices with web-based management interfaces that contained hidden backdoor links. These links are believed to have been planted by hackers who exploited known critical vulnerabilities during previous intrusions. The backdoors allowed unauthorized users to access internal device files, including system configurations, executables, and settings, through specific web URLs. Upon receiving the notification, the affected agencies reassessed the integrity of their system files, upgraded the devices to the officially recommended versions, and verified that no malicious files or programs were present, thereby assuring the overall security of their systems and environments.
【Additional Reference】
When a critical vulnerability is uncovered, it is possible that attackers have already taken advantage of it to breach multiple devices and install backdoors, allowing them to maintain access over time. Agencies are advised to not only apply patches immediately but also thoroughly inspect the integrity of system file structures, configuration settings, and access controls to ensure nothing suspicious has been left behind. At the same time, it is important to stay up to date with vendor advisories and various threat intelligence sources to stay informed about the latest attack methods and patching, to identify and eliminate potential risks as early as possible.