Cybersecurity Monthly Report (June 2025)
Cybersecurity Monthly Report (June 2025)
<Overall Threat Trends>
Ex ante joint defense and monitoring
This month, a total of 89,675 pieces of government agency cybersecurity joint defense intelligence were collected (a decrease of 2,957 from the previous month). Analyzing the types of identifiable threats, the top one was intrusion attacks (33%), mostly involving unauthorized access to systems or acquisition of system/user privileges, followed by information collection (30%), mainly obtaining information through attack methods such as scanning, detection, and social engineering, and intrusion attempts (26%), mainly dominated by attempts to intrude into unauthorized hosts. The distribution of intelligence volume in the past year is as shown in Figure 1.
After further compilation and analysis of joint defense information, it was recently discovered that hackers are suspected of leveraging compromised email accounts belonging to critical infrastructure personnel. They conducted social engineering email attacks targeting specific manufacturing companies using the subject line "Please Assist in Confirmation" and password-protected malicious compressed files. The aim was to bypass antivirus software and induce target recipients to open malicious attachments to steal sensitive computer data. Relevant intelligence has provided government agencies with recommendations on joint defense and monitoring protection.
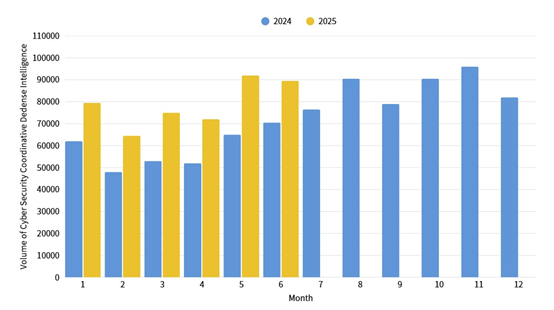
Figure 1: Statistics of cybersecurity monitoring intelligence in joint defense
In-process reporting and responding
The number of cybersecurity incident reports totaled 168 this month (an increase of 24 from the previous month), a 10.53% increase compared to the same period last year. This month saw more successful cases of attacks in exercises, primarily due to unsafe configuration settings, followed by injection attacks and ineffective access control incidents, accounting for 66.67% of the reported incidents this month. The statistics for cybersecurity incident reports over the past year are as shown in Figure 2.
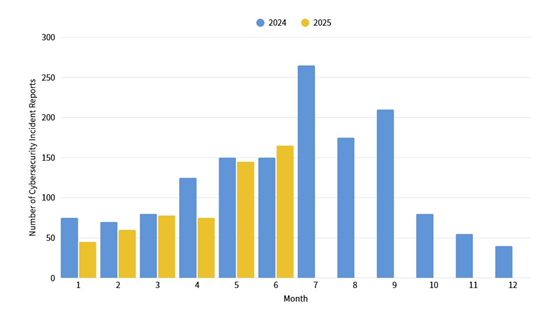
Figure 2: Statistics of cybersecurity incident reports
Post information sharing
This month, a government agency discovered that its public service phone was being used by unknown individuals for fraudulent calls. Investigation revealed that the public service phone was a Voice over IP (VoIP) device used by the agency. A comparison of call records showed external IP call activity, indicating that unauthorized dialing likely resulted from malicious external login to a VoIP gateway set up within the agency. Following the incident, the device's account passwords were immediately changed. After evaluating the device's future utility and security risks, it was decided to cease its use to prevent similar incidents from recurring.
If VoIP equipment lacks proper account/password settings, firewall, and monitoring mechanisms, it can easily become a vulnerability for fraudsters, leading to financial losses and damage to government trust. Recommendations for government agencies:
- Adhere to the "Deny by Default, Allow by Exception" Principle
To enhance maintenance convenience, remote access is often configured for maintenance personnel to troubleshoot or update. However, this can lead to underestimating device importance and neglecting access restriction management, potentially exposing systems to brute-force attacks, default credential attacks, or vulnerability exploitation. Therefore, the "deny by default, allow by exception" principle must be followed for system maintenance operations. (Regulations on Classification of Cyber Security Responsibility Levels - Schedule 10 - Defense standards of cyber systems - Access control) - Mandatory Use of Strong Passwords, Regular Updates, and Removal of Default Credentials
Some manufacturers publish product manuals online for user access, which may include default passwords. If these default passwords are not changed, they can easily be exploited by malicious actors. (Regulations on Classification of Cyber Security Responsibility Levels - Schedule 10 - Defense standards of cyber systems - Identification and authentication) - Evaluate Device Support for Regular Firmware Updates and Security Patches, Integrate into Management Processes, and Avoid Using End-of-Life or Unsupported Equipment
After devices are released, security vulnerabilities may be discovered that require patching through firmware updates. If a device is end-of-life or no longer receives security updates, it becomes a cybersecurity risk. It is recommended to integrate this into management processes, such as regularly inventorying update status and assessing whether retirement is necessary. (Compliance: Regulations on Classification of Cyber Security Responsibility Levels - Schedule 10 - Defense standards of cyber systems – Integrity of Systems and Information)