Cybersecurity Monthly Report (July 2025)
Cybersecurity Monthly Report (July2025)
1. Recent Policy Highlights
Phase Seven National Cyber Security Development Program (2025 - 2028) has the vision of "Building a Trustworthy and Secure Digital Society". It sets three major goals: "Strengthening the Cybersecurity Defense Resilience of the Entire Society," "Enriching the Cybersecurity Industry Ecosystem," and "Building New Defensive Technologies". The program proposes four implementation strategies : "Whole-of-Society Cyber Security Defense," "Enhancing Cyber Security Resilience of Critical Infrastructure," "Strengthening National Cyber Security Industry," and "Applications and Cooperation in Emerging Al Cyber Security Technologies". These strategies will be jointly promoted by central government ministries and local governments to maximize the overall effectiveness of the nation's cybersecurity joint defense.
2. Cybersecurity Trends
2.1 National Government Cybersecurity Threat Trends
Ex ante joint defense and monitoring
This month, a total of 92,214 pieces of government agency cybersecurity joint defense intelligence were collected (an increase of 2,539 pieces). Analyzing the types of identifiable threats, the top one was information collection (36%), mainly obtaining information through attack methods such as scanning, detection, and social engineering, followed by intrusion attacks (35%), which mostly involved unauthorized access to systems or the acquisition of system/user privileges , and intrusion attempts (20%), which were mainly dominated by attempts to intrude into unauthorized hosts. The distribution of intelligence volume in the past year is as shown in Figure 1.
Beware of Social Engineering Emails Posing as Product Quotations
After further compilation and analysis of joint defense intelligence, it was recently discovered that hackers were impersonating business-related product quotations and sending social engineering emails containing a rare .ARJ file extension. The file attachments were disguised with common file extensions (such as .pdf) to deceive recipients into clicking and opening the malicious file. Once the recipient executes the malicious program, it connects to Google Drive to download a second-stage malicious file, ultimately aiming to take control of the recipient's computer. Relevant intelligence has provided government agencies with recommendations on joint defense and monitoring protection.
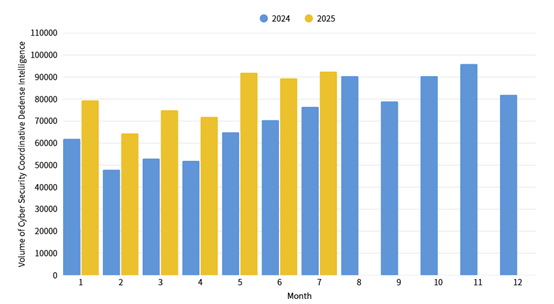
Figure 1: Statistics of cybersecurity monitoring intelligence in joint defense
In-process reporting and responding
The number of cybersecurity incident reports totaled 235 this month, a 12.64% decrease compared to the same period last year. The reported types were mainly illegal intrusions, with a continuous observation of multiple agency information systems having connections that exhibit backdoor characteristics, likely from the installation of counterfeit software. This accounted for 37.96% of the illegal intrusion reports this month. The statistics for cybersecurity incident reports over the past year are as shown in Figure 2.
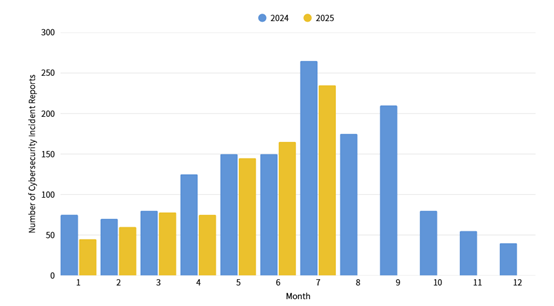
Figure 2: Statistics of cybersecurity incident reports
2.2 Important Vulnerability Alerts
| Alert Type | Category | Description |
|---|---|---|
| Vulnerability Alert |
Network Communication Equipment: Fortinet FortiWeb has a security vulnerability. Severity: CVSS 9.6 (CVE-2025-25257) |
|
|
System Platform: Cisco Unified Communications Manager has a high-risk security vulnerability. Severity: CVSS 10 (CVE-2025-20309) |
|
|
| Known Exploited Vulnerability |
Network Communication Equipment: Citrix | NetScaler ADC and Gateway Severity: CVSS 9.3, 8.7 (CVE-2025-5777, CVE-2025-5349) |
|
Alert Explanations:
Vulnerability Alert: Verified vulnerabilities that have not yet been widely exploited by attackers. It is recommended to arrange updates as soon as possible.
Known Exploited Vulnerability: Known instances of successful attacks exploiting the vulnerability. Immediate evaluation and patching are strongly recommended.