Cybersecurity Monthly Report (August 2025)
Cybersecurity Monthly Report (August2025)
1. Recent Policy Highlights
The draft amendment to the Cybersecurity Management Act was passed in its third reading by the Legislative Yuan on August 29, 2025. The Administration for Cyber Security will complete the revision of eight subordinate regulations within six months of being promulgated by the President, aiming to have them take effect simultaneously with the parent law. In addition, the Administration for Cyber Security will continue to strengthen the defense framework and real-time monitoring to effectively enhance network security protection and response capabilities, as well as promote overall defense resilience through the push for laws and policies.
2. Cybersecurity Trends
2.1 National Government Cybersecurity Threat Trends
Ex ante joint defense and monitoring
This month, a total of 89,438 pieces of government agency cybersecurity joint defense intelligence were collected (a decrease of 2,776 pieces). Analyzing the types of identifiable threats, the top one was intrusion attacks (36%), mainly involving unauthorized access to systems or acquisition of system/user privileges. This was followed by information collection (33%), which was primarily obtaining information through attack methods such as scanning, detection, and social engineering, and intrusion attempts (19%), which were mainly dominated by attempts to intrude into unauthorized hosts. The distribution of intelligence volume in the past year is as shown in Figure 1.
Beware of Malicious Emails Pertaining to Volunteer Program Applications
After further compilation and analysis of joint defense intelligence information, it was recently discovered that hackers used third-party email services (such as Microsoft Outlook and Google Gmail) to send social engineering emails with malicious attachments to government personnel, using the subject of a volunteer program application. The aim was to trick recipients into opening the malicious attachments to implant a backdoor program and then steal sensitive computer information. Relevant intelligence has provided government agencies with recommendations on joint defense and monitoring protection.
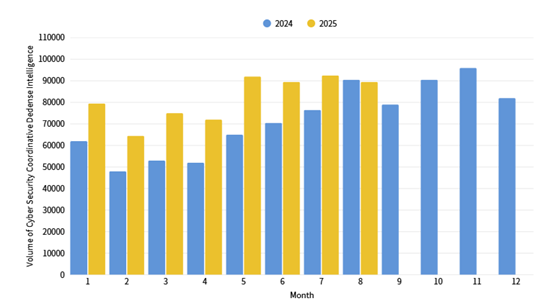
Figure 1: Statistics of cybersecurity monitoring intelligence in joint defense
In-process reporting and responding
The number of cybersecurity incident reports totaled 158 this month, a 9.20% decrease compared to the same period last year. There were more successful cases of attacks during exercises this month, accounting for 53.16% of the reported incidents. The primary cause was injection attacks, followed by incidents such as failed encryption mechanisms and ineffective access control. Statistics for cybersecurity incident reports over the past year are as shown in Figure 2.
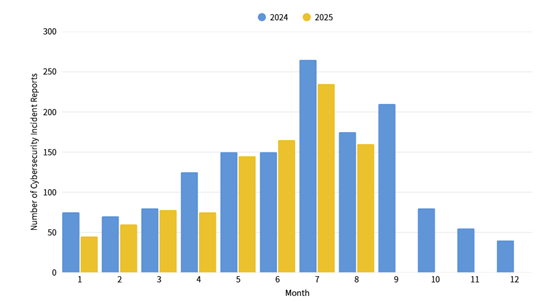
Figure 2: Statistics of cybersecurity incident reports
2.2 Important Vulnerability Alerts
| Alert Type | Category | Description |
|---|---|---|
| Vulnerability Alert |
Network Communication Equipment: Cisco Secure Firewall Management Center (FMC) Severity: CVSS 10 (CVE-2025-20265) |
|
| Known Exploited Vulnerability |
Network Communication Equipment: Citrix | NetScaler ADC and Gateway Severity: CVSS 9.2 (CVE-2025-7775) |
|
|
Windows Version of WinRAR: Severity: CVSS 8.4 (CVE-2025-8088) |
|
|
|
Trend Micro Apex One Severity: CVSS 9.4 (CVE-2025-54948 and CVE-2025-54987) |
|
Alert Explanations:
Vulnerability Alert: Verified vulnerabilities that have not yet been widely exploited by attackers. It is recommended to arrange updates as soon as possible.
Known Exploited Vulnerability: Known instances of successful attacks exploiting the vulnerability. Immediate evaluation and patching are strongly recommended.
3. Recent Cybersecurity Incident Sharing
Industrial Control Equipment Should Change Default Passwords and Restrict Exposure to the Internet
The National Institute of Cyber Security discovered that the control pages of some government agencies' industrial control equipment were not access-restricted, exposed to the internet, and had not changed their default login passwords. This month, an incident was discovered where one of these devices was successfully infiltrated and connected externally to a botnet. The agency subsequently assessed that remote operation was not a necessary requirement and took the compromised device offline. Future operations will be performed manually on-site by personnel.
Lessons Learned
Government agencies use industrial control environment equipment to manage business operations. Many of these devices may be located in remote or harsh environments, such as reservoirs or substations, which invisibly increases the cost and resources of on-site manual maintenance. Therefore, many operational units tend to monitor and maintain industrial control equipment through remote operations to reduce maintenance costs and improve operational efficiency. However, the failure to establish a complete defense framework (e.g., firewall or access control mechanisms) often leads to unrestricted or weakly controlled access, making industrial control equipment more susceptible to hacker attacks. This can result in significant risks to production lines, public safety, and operations. To address these issues, it is recommended that government agencies:
Establish a Secure and Monitored Remote Access Policy
Make remote access "secure and monitored". This includes whitelist control, setting up bastion hosts or VPN connections to avoid exposure to the public network, and using log records to continuously monitor the operator, time, and actions.
Implement Account Security for Industrial Control Equipment, Starting with Changing Default Passwords
Implement robust account and password management. The default passwords for some industrial control devices can be found in user manuals, official documents, or online forums. Hackers do not need to crack the password or use social engineering to gain successful access, which is a vulnerability most often exploited by many automated tools. It is recommended to change the original default password, set a password with sufficient length and complexity, and update it regularly. At the same time, follow the principle of least privilege to ensure that only authorized personnel can access and operate the equipment.
Immediately Patch Known Vulnerabilities to Consolidate Operational Security Patch known vulnerabilities as soon as possible and implement a vulnerability management policy. By promptly patching known vulnerabilities, you can not only reduce the possibility of equipment being attacked but also ensure the continued secure operation of industrial control systems, safeguarding operations and public safety.
4. International Cybersecurity News
Trend Micro Confirms: Critical Vulnerabilities in On-Premises Apex One Actively Exploited by Hackers (Source: SC Media)
Trend Micro has released a patch to address critical security vulnerabilities in the on-premises versions of its Apex One Management Console that have been actively exploited by hackers. The two vulnerabilities, CVE-2025-54948 and CVE-2025-54987, both have a high severity rating of 9.4 on the CVSS (Common Vulnerability Scoring System) and are classified as command injection and remote code execution vulnerabilities in the management console.
- CVE-2025-54948 stems from a lack of sufficient input validation in the backend of the management console, allowing a remote attacker with access to the management console interface to inject malicious operating system commands and achieve remote code execution.
- CVE-2025-54987 is similar to the former but targets a different CPU architecture.
Generally, a hacker would need physical or remote access and the ability to log into the Trend Micro Apex One management console to exploit these vulnerabilities. Trend Micro has released a temporary fix tool for the on-premises versions, with the official patch expected to be released in mid-August.
13 Countries Including US, UK, and Japan Jointly Warn that China-backed Hackers Have Infiltrated Global Critical Infrastructure (Source: Bleeping Computer)
According to a joint advisory published by the US National Security Agency (NSA), the UK National Cyber Security Centre (NCSC), and partners from other countries, the "Salt Typhoon" cyber espionage operation is linked to three China-based technology companies: Sichuan Juxinhe Network Technology Co., Ltd., Beijing Huanyu Tiangiong Information Technology Co., Ltd., and Sichuan Zhixin Ruijie Network Technology Co., Ltd. These three companies provide cyber products and services to China's Ministry of State Security and the People's Liberation Army.
The hacking group does not rely on zero-day vulnerabilities but instead exploits well-known and already-patched vulnerabilities on network edge devices. In the past, "Salt Typhoon" has infiltrated companies like AT&T, Verizon, and Lumen. The primary method is to use known vulnerabilities to establish backdoors in critical infrastructure across various countries to collect intelligence, targeting telecommunications, government, transportation, and military infrastructure. It is recommended to prioritize patching known vulnerabilities such as CVE-2024-21887 (Ivanti), CVE-2024-3400 (Palo Alto), CVE-2023-20273 (Cisco), CVE-2023-20198 (Cisco), and CVE-2018-0171 (Cisco). It is also advised to strengthen the security of network devices and enhance log monitoring. If using Cisco equipment, it is recommended to immediately disable Smart Install and Guest Shell.
5. Recent Key Cybersecurity Meetings and Activities
| Date | Event/Meeting | Audience |
|---|---|---|
|
September 24 |
The National Institute of Cyber Security (NICS) will hold a Product Cybersecurity Forum on September 24. The event aims to foster a shared understanding of responsibilities throughout the product cybersecurity ecosystem among industry, government, academia, and research sectors. |
Industry, Government, Academia |