Cybersecurity Monthly Report (September 2025)
Cybersecurity Monthly Report (September2025)
1. Recent Policy Highlights
The amendment to the Cyber Security Management Act was promulgated by the President on September 24, 2025, marking a crucial step forward in constructing our nation's cybersecurity legal framework. This legislative amendment not only addresses the challenges posed by the rapid changes in the domestic and international cybersecurity environment but also comprehensively strengthens the overall cybersecurity resilience of the government and society, establishing a more solid protective barrier for our nation's digital homeland security.
2. Cybersecurity Trends
2.1 National Government Cybersecurity Threat Trends
Ex ante joint defense and monitoring
This month, a total of 65,230 pieces of government agency cybersecurity joint defense intelligence were collected (a decrease of 24,208 pieces). Analyzing the types of identifiable threats, the top one was information collection (39%), which was primarily obtaining information through attack methods such as scanning, detection, and social engineering. This was followed by intrusion attempts (25%), which were mainly dominated by attempts to intrude into unauthorized hosts, and intrusion attacks (19%), mostly involving unauthorized access to systems or acquisition of system/user privileges. The distribution of intelligence volume in the past year is as shown in Figure 1.
Fake Petitions, Real Phishing: Hackers Target Official Channels to Launch Attacks
After further compilation and analysis of joint defense intelligence, it was discovered that hackers have recently sent social engineering phishing emails under the guise of "petitions" or "complaints." They primarily deliver malicious files through government agencies' relevant complaint channels (such as opinion mailboxes or official websites), attempting to lure recipients or the responsible government agency personnel into opening and executing the malicious attachments. Relevant intelligence has been provided to various agencies with recommendations for joint defense and monitoring protection.
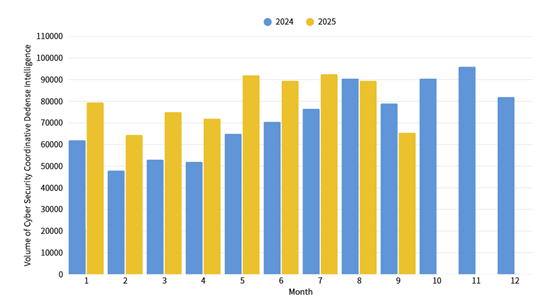
Figure 1: Statistics of cybersecurity monitoring intelligence in joint defense
In-process reporting and responding
The number of cybersecurity incident reports totaled 106 this month, a 49.76% decrease compared to the same period last year. The reported incident type was primarily illegal intrusion. The National Institute of Cyber Security (NICS) discovered that some agency information equipment showed connection characteristics of the PUBLOAD malicious program. After investigation by the agencies, most of these were found to be caused by USB drive infection. Statistics for cybersecurity incident reports over the past year are as shown in Figure 2.
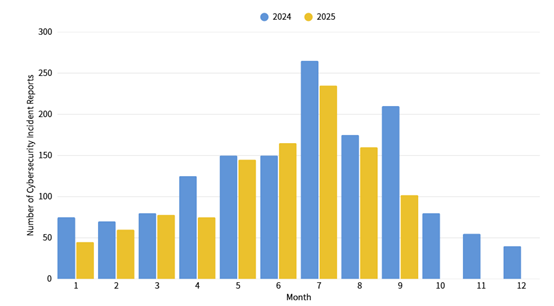
Figure 2: Statistics of cybersecurity incident reports
2.2 Important Vulnerability Alerts
| Alert Type | Category | Description |
|---|---|---|
| Vulnerability Alert |
Firewall Equipment: Cisco Secure Firewall Devices Have High-Risk Vulnerabilities |
|
| Known Exploited Vulnerability |
Firewall Equipment: Cisco Security Firewall Devices Have High-Risk Vulnerabilities |
|
|
Android Device: Android Runtime (ART) Use-After-Free Has High-Risk Vulnerability |
|
|
|
Web Application Platform: Web Application Servers Sitecore Experience Manager (XM) and Experience Platform (XP) Have High-Risk Vulnerability |
|
Alert Explanations:
Vulnerability Alert: Verified vulnerabilities that have not yet been widely exploited by attackers. It is recommended to arrange updates as soon as possible.
Known Exploited Vulnerability: Known instances of successful attacks exploiting the vulnerability. Immediate evaluation and patching are strongly recommended.
3. Recent Cybersecurity Incident Sharing
Beware of Petition Attachments! Fake PDF Shortcut Files Conceal Malware
The National Institute of Cyber Security (NICS) discovered malicious outbound connections from the information equipment of some agencies. Investigations by the agencies showed that the source of the intrusion was the petition channel provided on the official website. To process the petition case, the responsible personnel uncompressed the attached compressed file and reviewed the files one by one. They executed a shortcut (.lnk) file disguised as a PDF file, which resulted in the implantation of malicious software.
Lessons Learned
The National Institute of Cyber Security (NICS) has discovered that recent attackers are delivering files containing malicious programs through agency petition channels (such as opinion mailboxes), thereby luring responsible personnel into executing the malicious programs to achieve their intrusion goals. It is recommended that government agencies:
Strengthen File Security Inspection
Since compressed files may bypass common detection mechanisms, it is recommended to confirm the file name and actual format before decompression, avoid executing suspicious content, and enhance protection through antivirus scanning or sandbox testing.
Establish Standardized Procedures
For external source files, agencies should formulate guidelines for review and risk classification, and mandate that they be handled within a dedicated review environment or isolated platform. Corresponding security measures should be taken based on the different risk levels.
4. International Cybersecurity News
AI-Enhanced Malware Possesses Extremely High Stealth and Evasion Capabilities (Source: Dark Reading)
Researchers at the cybersecurity company Trend Micro have been tracking a malware campaign named "EvilAI." This campaign leverages seemingly legitimate AI tools and software to secretly implant malicious code, paving the way for future attacks. The campaign has currently affected hundreds of victims worldwide, spanning manufacturing, government, healthcare, and other industries across multiple countries, including the United States, India, the United Kingdom, Germany, France, and Brazil.
The hackers use applications named "App Suite", "Epi Browser", "Manual Finder" and others to disguise the malware. These programs feature professional user interfaces and functionalities to meet user expectations for such software. In most of these applications, the malicious code is generated by AI, allowing it to effectively evade scanning by antivirus software and threat detection tools.
To further increase the authenticity of these malicious programs, the hackers implement digital signatures using code-signing certificates acquired from newly registered entities. Once executed on the victim's device, the EvilAI application conducts extensive reconnaissance to map the victim's system environment and identify installed security products. After completing the reconnaissance, the EvilAI application forcibly terminates browser processes such as Microsoft Edge and Chrome and attempts to disable the victim's security protection products.
Official Prevention Recommendations
The FBI recommends that users take multiple preventative measures to avoid falling victim to similar scams, one of which is to directly type the official URL, www.ic3.gov/, into the browser instead of clicking a link via a search engine.
45 New Domains Linked to Salt Typhoon and UNC4841 Exposed (Source: Silent Push)
The cybersecurity company Silent Push has discovered 45 new domains, some of which can be traced back as far as 2020. These domains are linked to the Chinese hacking groups Salt Typhoon and UNC4841 and are being used for cyber-espionage activities.
These domains were registered by individuals using pseudonyms and false addresses, allowing the hackers long-term and covert access to target organizations, particularly in the telecommunications sector.
Due to the highly persistent nature of the Salt Typhoon attack method and the overlap of its infrastructure with other Chinese-sponsored groups, it continues to pose a threat. Therefore, organizations should immediately check their DNS logs for any activity related to these domains and IP addresses to guard against potential intrusion.
Please refer to the following URL for the list of new domains used as attack indicators by Salt Typhoon and UNC4841: https://www.silentpush.com/blog/salt-typhoon-2025/
5. Recent Key Cybersecurity Meetings and Activities
| Date | Event/Meeting | Audience |
|---|---|---|
|
September 24 |
Product Cybersecurity Forum: Jointly Building the Product Cybersecurity Responsibility Chain. |
Industry, Government, Academia |
| September 25 - October 27 | Product Cybersecurity Vulnerability Hunting Program | Industry |