Cybersecurity Monthly Report (October 2025)
Cybersecurity Monthly Report (October2025)
1. Recent Cybersecurity Incident Sharing
Weak Passwords Based on Common Keyboard Patterns Are Easily Compromised
An agency received a notification from its Security Operations Center (SOC). The notification indicated abnormal outbound connections from a system intended solely for internal use. Upon investigation, it was determined that during a recent firewall replacement, firewall policies were not individually verified to ensure proper enforcement. As a result, the internal system was exposed to external access and subsequently compromised, as it employed weak passwords based on common keyboard patterns, resulting in successful brute-force attacks, unauthorized access, and the deployment of malicious software. In response, the agency rebuilt the affected system in a virtualized environment, enforced comprehensive password changes, and required administrators to comply with password complexity principles, strictly prohibiting the use of keyboard-based password patterns.
Lessons Learned
Although the agency had implemented the Government Configuration Baseline (GCB) in accordance with regulatory requirements, user account passwords were still created using predictable keyboard sequences (such as “1qaz2wsx” and “!QAZ@WSX”). While these passwords formally met GCB requirements for length and complexity, their high predictability allowed brute-force tools to successfully guess login credentials, indicating insufficient security awareness. Furthermore, changes to network devices and configuration settings should be subject to proper validation, testing, and continuous monitoring to reduce cybersecurity risks. Agencies are therefore advised to adopt the following measures:
Introduce multi-factor authentication for high-protection systems
For information systems classified as having a “high” protection requirement, agencies are advised to implement Multi-Factor Authentication (MFA) to strengthen identity authentication security.
Enforce configuration change validation and regular audits
Establish change management mechanisms for network devices and configurations, including pre- and post-change validation procedures to ensure that settings are fully and correctly applied. Regular audits should be conducted to review firewall rules and access logs to identify unintended exposures or misconfigurations.
Enhance detection of abnormal login behavior
Strengthen detection and monitoring mechanisms, such as tracking failed login attempts, unusual login times, and high volumes of login attempts within short periods, enabling early detection of abnormal access, repeated attacks, or brute-force activities.
2. Cybersecurity Trends
2.1 National Government Cybersecurity Threat Trends
Ex ante joint defense and monitoring
This month, a total of 58,621 pieces of government agency cybersecurity joint defense intelligence were collected (a decrease of 6,609 pieces). Analysis of identifiable threat categories shows the top one was information collection (38%), mainly involving the acquisition of information through attack methods such as scanning, detection, and social engineering. This was followed by intrusion attempts (26%), which were mainly involving attempts to intrude into unauthorized hosts, and intrusion attacks (18%), most of which involved unauthorized system access or the acquisition of system or user privileges. The distribution of cybersecurity intelligence over the past year is illustrated in Figure 1.
Hackers Abuse Legitimate Websites to Distribute Malware
Further compilation and analysis of joint cyber defense intelligence indicates that attackers have recently abused the Internet Archive, a legitimate digital library service providing access to archived web content and multimedia resources, as a malware download platforms in social engineering phishing emails. By leveraging a trusted and legitimate domain, attackers were able to distribute malicious software while evading cybersecurity detection mechanisms. Relevant intelligence and defensive recommendations have been provided to government agencies for joint monitoring and protection.
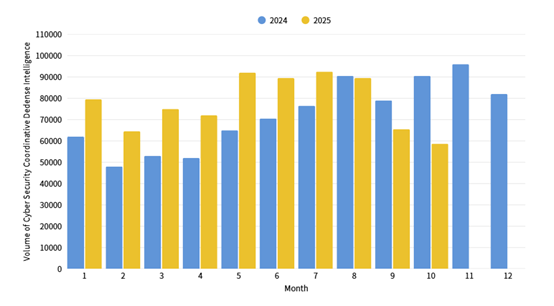
Figure 1: Statistics of cybersecurity monitoring intelligence in joint defense
In-process reporting and responding
This month, a total of 53 cybersecurity incidents were reported, representing a 32.91% decrease compared to the same period last year. The primary type of reported incident was illegal intrusions, accounting for 58.49% of all reported cases. Notably, some agencies continued to experience PUBLOAD malware infections introduced via portable media. In addition, incidents were observed in which surveillance cameras were compromised and exploited to download malicious scripts. Statistics on cybersecurity incident reports over the past year are illustrated in Figure 2.
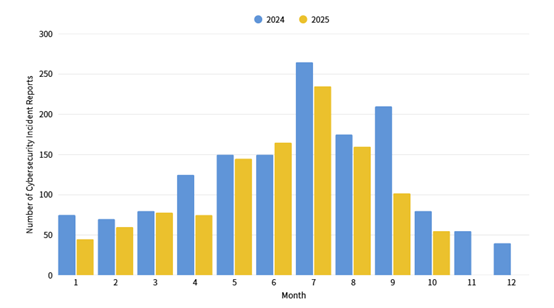
Figure 2: Statistics of cybersecurity incident reports
2.2 Important Vulnerability Alerts
| Alert Type | Category | Description |
|---|---|---|
| Vulnerability Alert |
System Services: Excellent Infotek Document Management System |
|
| Known Exploited Vulnerability |
Microsoft Windows Server: Windows Server Update Services (WSUS) Has High-Risk Vulnerability |
|
|
Microsoft Windows Server: Windows SMB Has High-Risk Security Vulnerabilities |
|
|
|
VMware Tools Have High-Risk Security Vulnerabilities |
|
Alert Explanations:
Vulnerability Alert: Verified vulnerabilities that have not yet been widely exploited by attackers. It is recommended to arrange updates as soon as possible.
Known Exploited Vulnerability: Known instances of successful attacks exploiting the vulnerability. Immediate evaluation and patching are strongly recommended.
3. International Cybersecurity News
Google Patches “Gemini Trifecta” Vulnerabilities in Gemini AI Suite (Source: Hack Read)
Security firm Tenable identified three critical vulnerabilities in Google’s Gemini AI assistant suite, collectively referred to as the “Gemini Trifecta” . Disclosed in early October, these vulnerabilities exposed Gemini to risks, such as prompt injection and data exfiltration, potentially threatening user data security.
Details of the Three Key Vulnerabilities
Vulnerability 1: Prompt Injection via Chrome Browsing History
- Affected Component: Gemini Search Personalization Model
- Attack Method: Attackers can manipulate a user’s Chrome browsing history.
- Potential Impact: This may enable prompt injection, allowing attackers to influence or control the AI’s output and behavior.
Vulnerability 2: Malicious Log Entries and Cloud Resource Exploitation
- Affected Component: Gemini Cloud Assist
- Attack Method: Attackers embed malicious prompts into log entries, such as through the HTTP User-Agent field in web requests.
- Potential Impact: This may facilitate phishing attacks and lead to unauthorized operations on cloud resources.
Vulnerability 3: Defense Bypass and Private Data Exfiltration
- Affected Component: Gemini Browsing Tool
- Attack Method: Attackers can bypass Google’s defensive mechanisms.
- Potential Impact: This may result in data exfiltration, allowing private user information (such as location data) to be transmitted to external servers.
Google has rolled back the affected models, disabled the rendering of malicious hyperlinks, and deployed layered defenses against prompt injection across the entire Gemini suite.
Human Risk Report Reveals Corporate Overconfidence in Phishing Defense (Source: TechRepublic)
The annual Human Risk Behavior Snapshot released by Arctic Wolf shows that, despite strong confidence in their cybersecurity defenses, many organizations remain vulnerable to data breaches driven by employee behaviors—specifically phishing lapses and risky AI usage habits. The report shows that 68% of IT leaders reported experiencing a data breach in 2025, reflecting an increase of 8% over the previous year.
- Gap Between Overconfidence and Actual Risk:
Despite nearly two-thirds of IT leaders and half of employees acknowledged having clicked on malicious links, approximately 75% of leaders still believed their organizations were secure. Leadership’s excessive confidence in defensive measures, coupled with employees’ tendencies to circumvent security policies, has widened the gap between perceived security posture and actual vulnerabilities. - Information Risks Introduced by Generative AI:
As the adoption of generative AI continues to increase, information security risks have also intensified. The report shows that 80% of IT leaders and 63% of employees use AI tools in their work, with 60% of leaders and 41% of employees admitting to having input confidential data into these platforms. - Diverging Approaches to Human Error:
The report further highlights growing divergence in how organizations respond to human error. Companies that focus on corrective training successfully reduced risk by 88%. However, 77% of IT leaders indicated that they would dismiss employees who fell victim to scams, an increase from 66% in the previous year.
Simple Prompt Injection Attacks Can Bypass OpenAI Guardrails (Source: Hack Read)
After OpenAI released its AgentKit toolkit on October 6 and simultaneously introduced the Guardrails security framework, cybersecurity firm HiddenLayer disclosed a significant flaw in the framework.
OpenAI describes Guardrails as an open-source, modular security layer that leverages special AI programs namely LLM-based “judges” to prevent malicious behaviors such as jailbreaks and prompt injections. However, HiddenLayer identified a method to bypass these Guardrails.
The researchers noted that when the model used to generate responses is of the same type as the model used for security evaluation, both models can be deceived in similar ways. They successfully disabled primary security detectors and induced the system to generate harmful responses while executing hidden prompt injections.
In one test case, HiddenLayer manipulated the AI judges’ confidence scores, allowing them to bypass a detector that originally had 95% confidence in classifying the prompt as a jailbreak attempt. The researchers further demonstrated that the system could be deceived into allowing indirect prompt injections via tool calls, potentially resulting in the leakage of users’ sensitive data.
4. Recent Key Cybersecurity Meetings and Activities
| Date | Event/Meeting | Audience |
|---|---|---|
|
November 13 (All day) |
Government Cybersecurity Seminar (Kaohsiung) |
Government agencies, CI CISOs |