Cybersecurity Monthly Report (November 2025)
Cybersecurity Monthly Report (November2025)
1. Recent Policy Highlights
The amendment to the Cyber Security Management Act was promulgated by the President on September 24, 2025, and will come into effect on December 1, 2025.
In addition, seven related subordinate regulations (Tentative) namely the Enforcement Rules of Cyber Security Management Act, Regulations on Classification of Cyber Security Responsibility Levels, Regulations on Audit of Implementation of Cyber Security Maintenance Plan, Regulations on the Notification and Response of Cyber Security Incident, Regulations Governing the Handling of Cyber Security Matters of Government Agency Personnel, Cyber Security Information Sharing Regulations, and Regulations on the Review of Products Endangering National Cyber Security are scheduled to take effect on January 1, 2026.
2. Recent Cybersecurity Incident Sharing
Case 1
Fake Chrome Extension Update Prompt Leads to System Compromise
During a cybersecurity health check, an agency detected suspicious files on a workstation. Following SOC forensic analysis, the files were determined to be high-risk, and abnormal outbound connections were identified. Further investigation revealed that the incident originated when a staff member browsed websites on an office computer after working hours and encountered a pop-up window prompting an update to a Chrome extension. The user mistakenly believed the prompt to be a legitimate update notification and followed the instructions, resulting in the download of malicious software. The agency has since reinstalled the operating systems on the compromised devices while simultaneously organizing cybersecurity awareness training for its users.
Lessons Learned
In recent years, attackers have increasingly disguised malicious software as system updates or browser extension updates, luring users to download malware through look-alike interfaces. In the absence of effective browser or endpoint protection mechanisms, such tactics may become an entry point for malware into endpoints. Agencies can mitigate the risk of downloading malware via fake update prompts by strengthening browser controls, restricting unauthorized extensions and executable files, and enhancing user discernment.
Implement software installation controls at the source, adopt an application whitelisting approach, and enable pop-up blocking mechanisms
Strengthen browser and extension controls by adopting a whitelisting mechanism, enabling pop-up blocking, and centrally managing the deployment of browser and extension updates by administrators, thereby reducing users’ exposure to fake update prompts.
Strictly control software execution authorization to prevent abnormal program activity
Restrict unauthorized programs and abnormal activities by using Group Policy Objects (GPO) to block the execution of unsigned or unknown-source programs, and implementing tiered whitelisting controls to balance operational requirements and security protection.
Enhance personnel cybersecurity awareness to identify spoofing and social engineering traps
Enhancing security awareness: strengthen training to empower personnel to recognize fake update prompts, spoofed download pages, and suspicious pop-up windows, thereby minimizing the risk of accidental clicks and malware installation.
Case 2
Weak Password and Personal-Official Account Mixing Lead to Government Social Media Account Takeover
An agency established a Facebook fan page for public outreach purposes, which was jointly managed by a staff member and a maintenance vendor. However, the staff member’s personal Facebook account was compromised due to the use of a weak password. As a result, the management authorization of the agency’s fan page linked to the personal account were affected, and all original administrators (the staff member and the vendor) were removed.
The agency reported the incident to the Criminal Investigation Bureau of the National Police Agency, which coordinated with Meta to restore the original administrator privileges. Subsequently, all involved personnel were required to change their passwords, conduct account reviews, and verify Facebook security settings.
Lessons Learned
Official government social media pages should not be managed via personal accounts. Such accounts are often susceptible to risks—including third-party app integrations, cross-device logins, password reuse, and the absence of multi-factor authentication (MFA)—all of which may lead to inconsistent security postures. These vulnerabilities heighten the risk of account compromise or Access Token abuse. Accordingly, agencies are advised to strengthen account security controls, restrict linked applications, and perform periodic reviews.
Enable multi-factor authentication and security settings
- Enable Multi-Factor Authentication (MFA).
- Use strong, unique passwords and establish periodic password rotation.
- Enable Login Alerts and regularly review login locations, logged-in devices, and authorized browsers.
- Enable trusted device management to reduce the risk of unauthorized access.
Regularly review authorized and linked applications
- Periodically review authorized third-party applications under Facebook “Apps and Websites.”
- Remove unknown or unused applications to prevent OAuth Token abuse.
- Monitor authorization status of external tools related to fan page management (e.g., scheduling or advertising tools).
3. Cybersecurity Trends
3.1 National Government Cybersecurity Threat Trends
Ex ante joint defense and monitoring
This month, a total of 62,795 cybersecurity joint defense intelligence items were collected from government agencies, (an increase of 4,174 items). Among identifiable threat categories, information collection ranked first (41%), primarily involving scanning, detection, and social engineering techniques. This was followed by intrusion attempts (23%), mainly targeting unauthorized hosts, and intrusion attacks (18%), which mostly involved unauthorized system access or the acquisition of system or user privileges. Statistics on the distribution of intelligence over the past year are shown in Figure 1.
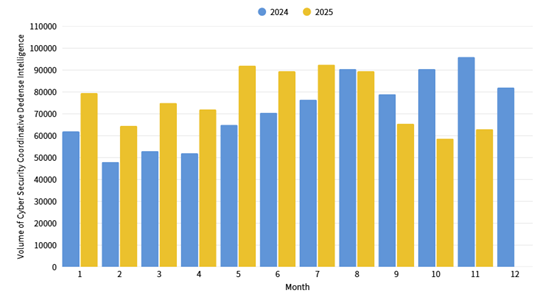
Figure 1: Statistics of cybersecurity monitoring intelligence in joint defense
Hackers Hide Malware on Legitimate Websites to Evade Detection
After further compilation and analysis of joint defense intelligence, it was recently discovered that attackers have abused the free cloud file-sharing service CatBox as a malware download site in social engineering phishing emails. The platform provides file upload and download link generation for file access and sharing. By leveraging its legitimate domain, attackers were able to distribute malicious software in order to evade cybersecurity detection mechanisms. Relevant intelligence and defensive recommendations have been provided to government agencies for joint monitoring and protection.
In-process reporting and responding
The number of cybersecurity incident reports totaled 72 this month, representing a 35.85% increase compared to the same period last year. The primary type of reported incidents were illegal intrusions, accounting for 58.40% of the total cases. Specific cases involved PUBLOAD malware infections introduced via portable media; furthermore, Network Video Recorder (NVR) were compromised and exploited to download Linux malware using Curl commands. Statistics for cybersecurity incident reports over the past year are shown in Figure 2.
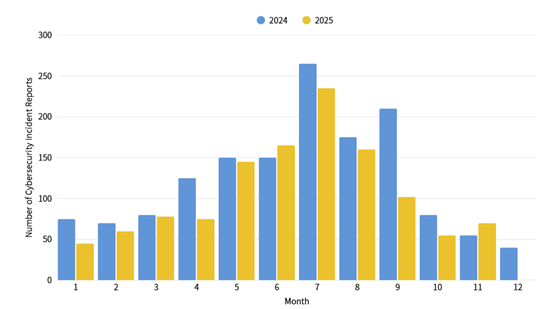
Figure 2: Statistics of cybersecurity incident reports
2.2 Important Vulnerability Alerts
| Alert Type | Category | Description |
|---|---|---|
| Vulnerability Alert |
User/Server Software: Samba Remote Code Execution Vulnerability |
|
| Network Communication Equipment: ASUS DSL Routers High-Risk Security Vulnerability Severity: CVSS 9.3 (CVE-2025-59367) |
|
|
| Network Management Platform: Cisco Catalyst Center Virtual Appliance High-Risk Security Vulnerability Severity: CVSS 8.8 (CVE-2025-20341) |
|
|
| Known Exploited Vulnerability |
Network Communication Equipment: Fortinet FortiWeb: Path Traversal RCE (Remote Code Execution) & OS Command Injection Vulnerabilities |
|
|
Server/Application: Oracle Fusion Middleware Privilege Escalation Vulnerability |
|
Alert Explanations:
Vulnerability Alert: Verified vulnerabilities that have not yet been widely exploited by attackers. It is recommended to arrange updates as soon as possible.
Known Exploited Vulnerability: Known instances of successful attacks exploiting the vulnerability. Immediate evaluation and patching are strongly recommended.
4. International Cybersecurity News
CISA: Ransomware Groups Actively Exploiting High-Risk Linux Vulnerability (Source: Bleeping Computer)
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) have confirmed that a high-risk privilege escalation vulnerability in the Linux kernel, CVE-2024-1086, is being actively exploited by ransomware groups. Disclosed on October 31, 2024, the vulnerability is a use-after-free flaw in the netfilter: nf_tables component. Successful exploitation allows attackers with local access to escalate authorization potentially gaining root access to affected systems. According to Immersive Labs, attackers obtaining root authorization may conduct system takeovers, lateral movement, and data exfiltration. The vulnerability affects major Linux distributions, including Debian, Ubuntu, Fedora, and Red Hat, across kernel versions 3.15 to 6.8-rc1. CISA added the vulnerability to its Known Exploited Vulnerabilities (KEV) catalog on October 22 and set November 12 as the mandatory remediation deadline for federal agencies.
UK NHS England Warns of Actively Exploited 7-Zip Vulnerability (CVE-2025-11001) (Source: Help Net Security)
NHS England Digital issued a warning that the 7-Zip vulnerability CVE-2025-11001 is being actively exploited. The vulnerability is a path/directory traversal flaw related to the handling of symbolic links in ZIP archives, allowing crafted ZIP files to traverse unintended directories. Attackers may exploit this flaw by executing code under a service account. The vulnerability is exploitable only on Windows systems and requires administrator or service account privileges, or Windows systems with Developer Mode enabled. As 7-Zip does not support automatic updates, users are strongly advised to upgrade to the latest version (fixed in v25.00) as soon as possible.
5. Recent Key Cybersecurity Meetings and Activities
| Date | Event/Meeting | Audience |
|---|---|---|
|
December 18 |
46th Council Meeting, NICST, Executive Yuan |
Council commissioners, government agencies |