Cybersecurity Monthly Report (July 2023)
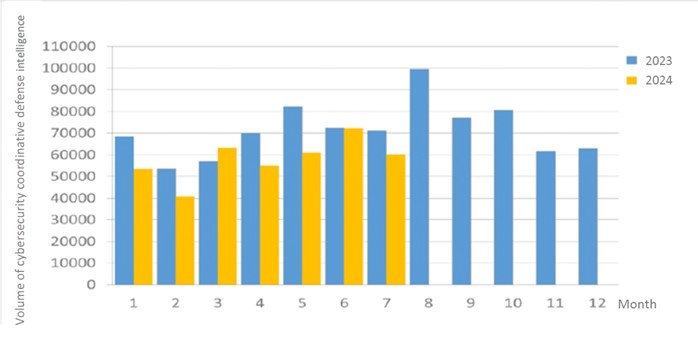
Figure 1 Statistics of cybersecurity monitoring intelligence in joint defense
In-process reporting and responding
There were a total of 117 cybersecurity incident reports this month, of which agencies' external network disrupted due to problems with the Internet Service Providers (ISPs) accounted for 25% of the incidents related to "equipment issues." In addition, the statistics of cybersecurity incident reports in the past year are as shown in Figure 2.
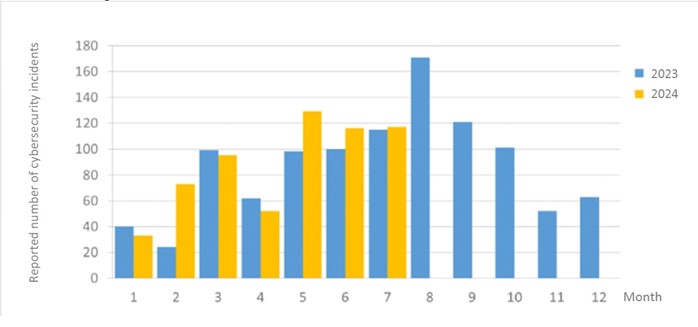
Figure 2 Number of reported cybersecurity incidents
Post information sharing
This month we received a report from an agency that several of their observation post hosts were attacked by ransomware. After investigation, we found that the source of the attack was a vendor-maintained computer in an observation post. The hackers successfully logged into the computer maintained by the vendor. Using the equipment as a jump server, hackers launched attacks through remote desktop by connecting to multiple observation post hosts. Upon further analysis, it was discovered that some of the agency's observation post hosts are set up in remote areas and are difficult to maintain, which is why maintenance vendors are commissioned for the task in a remote way. The agency has changed the account password of the hacked equipment while restricting access to the maintenance vendor's computer. Centralized management was implemented for the observation post hosts to decrease the risk of intrusion.
Additional Reference:
The commissioning of external vendors to perform remote maintenance of information systems for agencies should be conducted by adopting the doctrine of “prohibited in principle, permitted as exceptions.” If implementation is necessary, it must be compliant with Article 4 of the Enforcement Rules of Cyber Security Management Act and Schedule 10 of the Regulations on Classification of Cyber Security Responsibility Levels, where a management mechanism according to remote access requirements should be established and implemented. In addition, identical account passwords should be avoided across different information devices to reduce cybersecurity risks.