Cybersecurity Monthly Repor(August 2023)
Ex ante joint defense and monitoring
A total of 59,498 pieces of government agency cybersecurity joint defense intelligence were collected this month, analyzing the types of identifiable threats. The top identifiable threat was information collection (47%), i.e., mainly obtaining information through attacks such as scanning, detection and social engineering. This was followed by hacking attempts (22%), which were mainly attempts to hack unauthorized hosts; and intrusion attacks (14%), most of them involving unauthorized access to systems or acquisition of system/user privileges. In addition, the distribution of intelligence volume in the past year is as shown in Figure 1.
After further compilation and analysis of joint defense intelligence, it was discovered that hackers have recently impersonated an organization and used subjects related to the organization's business to send social engineering e-mails to attack devices of government agencies and the general public. Analysis shows that hackers stole the contents of e-mails that people had exchanged with the organization in the past, using them as bait to include malicious attachments. The large scale spreading of malicious spam e-mails (Malspam) was used to carry out social engineering attacks, stealing personal information by implanting backdoor programs. The relevant information has been provided to agencies with recommendations for joint defense, monitoring and protections.
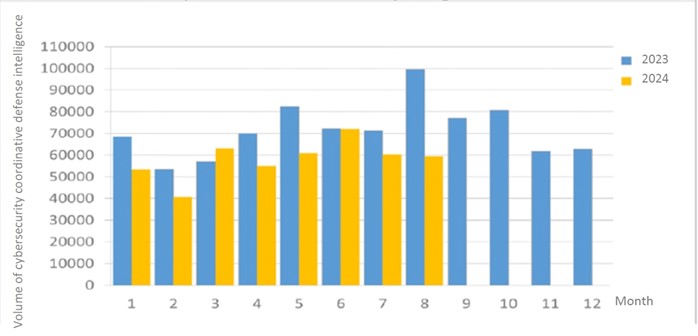
Figure 1 Statistics of cybersecurity monitoring intelligence in joint defense
In-process reporting and responding
A total of 130 cybersecurity incidents were reported this month and the number of reported incidents this month decreased by 23.98% compared with last year. This was mainly due to the fact that during the same period last year, it was discovered that multiple agencies used a vulnerable third-party application bundle, CKEdito, and were successfully attacked. During this year’s training drill, vulnerabilities related to each agency have been improved. In addition, the statistics of cybersecurity incident reports in the past year are as shown in Figure 2.
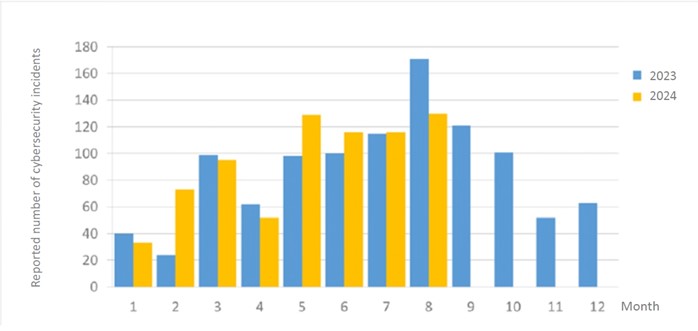
Figure 2 Number of reported cybersecurity incidents
Post information sharing
This month, an agency detected a web-based Trojan uploaded to their website. After investigation, it was found that the website had a vulnerability in the Microsoft IIS tilde directory enumeration. Hackers exploited the vulnerability to download backup source code files stored on the website by the vendor. Furthermore, it was found that the upload function can be accessed without authentication. The upload function was then utilized to implant malicious programs. The agency subsequently patched the vulnerability and removed the website’s source code backup files.
To maintain the convenience of their websites, some information vendors back up source code on the website's host, thus exposing it to the open network. Hackers can use tools such as Dirb directory scanning to scan the web page path and obtain these files. This allows the hackers to explore vulnerabilities or obtain sensitive information such as keys, which can be modified to gain unauthorized access. It is recommended that external service systems should comply with internal standards, undergoing information security testing before going online, receiving regular vulnerability scanning and penetration testing, and establishing a program source code management mechanism. This can be done through off-site backup, control, access of audit trail records, and original source code verification for older versions of the program to backup and archive files so as to reduce cybersecurity risks.