Cybersecurity Monthly Report (October 2023)
Ex ante joint defense and monitoring
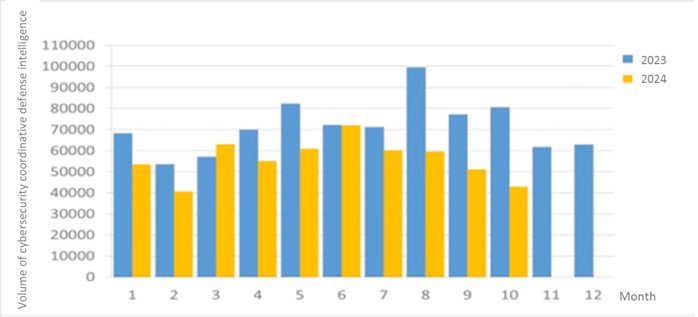
A total of 42,972 pieces of government agency cybersecurity joint defense intelligence were collected this month, analyzing the types of identifiable threats. The top identifiable threat was information collection (49%), i.e., mainly obtaining information through attacks such as scanning, detection and social engineering. This was followed by hacking attempts (23%), which were mainly attempts to hack unauthorized hosts; and intrusion attacks (10%), most of them involving unauthorized access to systems or acquisition of system/user privileges. In addition, the distribution of intelligence volume in the past year is as shown in Figure 1.
After further compilation and analysis of joint defense intelligence, it was found that the nuclear wastewater discharge performed by a certain country has recently attracted global attention. Hackers used the e-mail accounts of private companies in that country to send social engineering e-mails containing malicious compressed files on the grounds of nuclear wastewater revelations. These e-mails were used to conduct social engineering e-mail attacks on specific government agencies. The relevant information has been provided to agencies with recommendations for joint defense, monitoring and protections.
In-process reporting and responding
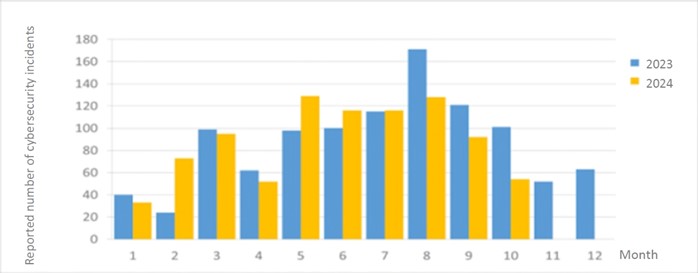
There were a total of 54 information security incident reports this month, a decrease of 46.53% compared with the same period last year. This was mainly due to a decrease in the number of incidents related to botnet attacks, which was approximately 80.95% lower than the same period last year. In addition, the statistics of cybersecurity incident reports in the past year are as shown in Figure 2.
Post information sharing
This month, the National Institute of Cyber Security detected the connection of a malicious program in an agency. After an investigation launched by the agency, it was found that an employee downloaded and installed communication software on the office computers due to business needs, but did not download the official version from the official website. This resulted in installation of the malicious program, which initiated external connections. The agency has rebuilt the compromised computer and reinforced internal cybersecurity education, requesting employees to refrain from installing non-official software on official devices. If necessary for business purposes, software should be downloaded from official websites to avoid downloading installation files containing malicious programs.
Communication software has become the primary tool for communication at work. Hackers have also taken advantage of this trend and created installation files containing malicious programs for popular communication software, distributing them in large quantities across the Internet. If users do not pay attention to the source of files when searching for software tools, they may download installation files containing malicious programs, allowing hackers to successfully invade the users' computer. Agencies should establish regulations and restrictions on internal downloading and installation of software, prohibiting personnel from installing unauthorized or non-official software on office equipment. If software is installed for business needs, they should be downloaded from the official website of the software to decrease the risk of hacking.